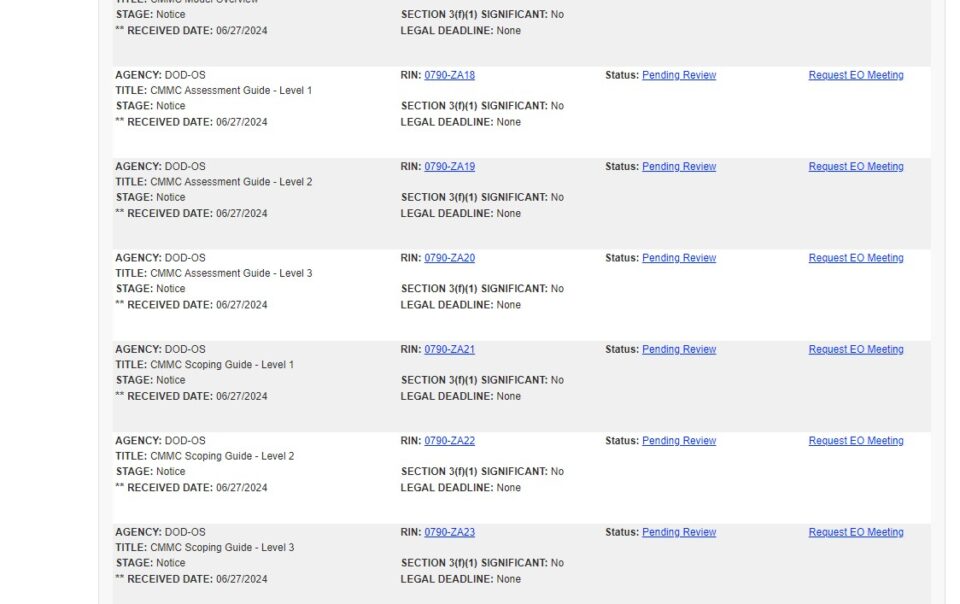
In our first CMMC Practice session we reviewed the Level 1 Practices within the Access Control (AC) Domain. Switching our CMMC practice focus from Federal Contract Information (FCI) to Controlled Unclassified Information (CUI), in this session we take a more […]
-
| Services
-
| Industries
-
| CMMC/800-171
-
| CyberMD™
-
| About
-
| Catapult®