Penetration Testing & Vulnerability Assessment.
Penetration Test (Pentest) is a simulated cyber-attack that evaluates your network’s defenses by using the same tools and techniques as real-world attackers. Think of it as testing the locks on your digital back door—if vulnerabilities exist, bad actors will exploit them unless you find and fix them first. Pentests help protect your company’s assets, intellectual property, and customer data by uncovering weaknesses and providing actionable steps to fortify your security.
Why Your Business Needs a Penetration Test.
In today’s connected world, every internet connection is a potential gateway for attackers. Without proper security measures, your network is as vulnerable as an unlocked glass door, leaving your sensitive data exposed. A Pentest identifies these weak points, helping you secure your systems and keep unauthorized users out. If you don’t find the vulnerabilities, the bad actors will.
What Does a Penetration Test Do?
Penetration Testing is designed to:
- Identify weaknesses in your network and associated systems.
- Assess the effectiveness of existing controls, systems, and sensors.
- Detect unforeseen vulnerabilities in hardware, software, and configurations.
- Provide data-driven insights to refine your cybersecurity strategies, remediation efforts, and budgets.
- Support compliance with federal laws and industry regulations.
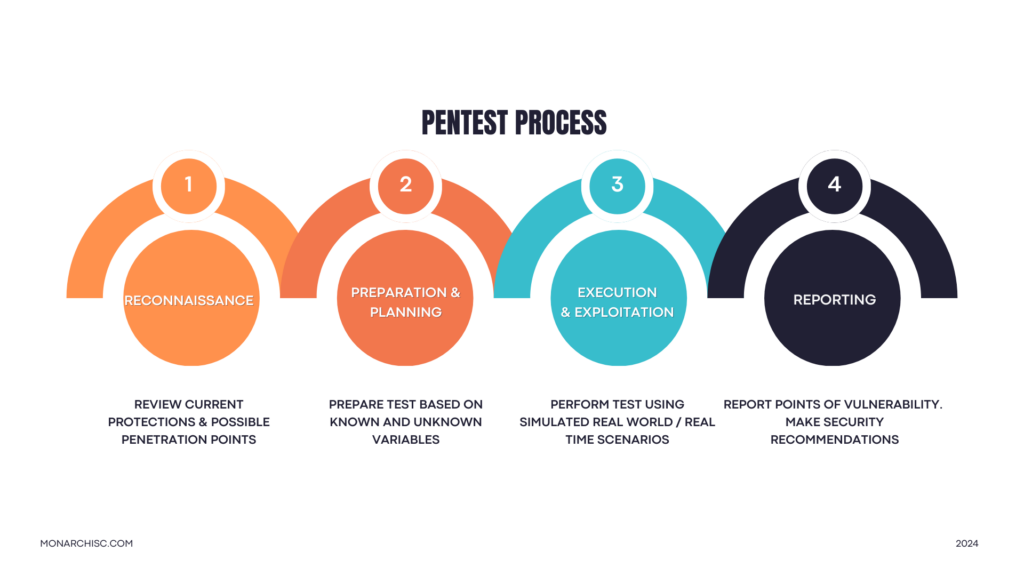

The Pentest Process
Reconnaissance Preparation & Planning.
The Pentest Team gathers intelligence about your network from public and private sources. This involves scanning your systems with advanced tools to uncover potential weaknesses and points of entry.
Access:
Using the collected intel, testers attempt to gain entry into your systems and maintain access long enough to demonstrate their ability to manipulate systems, steal data, corrupt software, or suspend services, just as an actual attacker might.
Reporting:
After testing, a detailed report outlines the vulnerabilities discovered, their potential impacts, and recommended remediation steps to close security gaps effectively.
Pentests are tailored to your specific operations, anticipated vulnerabilities, and exposure risks, covering:
- Wi-Fi and hardwired networks.
- Mobile devices and cloud environments.
- Embedded devices, web and mobile apps.
- Patching processes and APIs.
Why Choose Monarch ISC for Penetration Testing?
Our professional Pentest Team are experts trained to think like hackers, targeting and analyzing attacks in ways automated tests cannot. Their hands-on experience ensures thorough assessments, uncovering vulnerabilities that are often missed by generic tools. With Monarch ISC, you gain actionable insights and tailored recommendations to keep your business safe from ever evolving threats.





